
PII, or personal identifiable information is a type of data that can be used to track a specific individual. It includes identity details, location data, or contact information. That’s why it is necessary to keep PII private to keep your identity safe. According to a report by an UpGuard analyst, in 2021, Microsoft Power App suffered a data breach attack that exposed 38 million records containing personally identifiable information (PII). It happened because of the Open Data Protocols (OData) API used by the organization’s Power Apps portal, which contained an anonymously accessible list of data.
As of today, there are various methods to record, track, and utilize your personal data. The fingerprints and facial scans can unlock the devices, which makes it more crucial to take necessary measures to protect identity and other information that are unique to a person. Securing PII is important to ensure that integrity of your identity remains secure. Otherwise with just a few bits of personal information, bad actors can create false accounts in your name.
Types of PII
PII is of two types: Sensitive and Non- Sensitive.
- Sensitive PII: It includes all such information which contains your full name, address, or financial information. This type of data requires encryption to prevent harm being caused to the individual if their PII ends up in the wrong hands.
- Non-Sensitive PII: This includes any generic data accessible from public resources such as social media profiles that cannot be used to identify a specific individual. This type of information is often readily available and even transmitted without any encryption does not cause any harm.
Why Is It Important to Secure PII?
- Threat actors can use compromised PII to launch cyber-attacks and social media scams in order to steal financial information.
- PII is a reason for websites to be subject to constant attacks hence, multiple layers of security are very important to put in place.
- Data privacy, ownership and visibility will be put at risk if companies do not secure the PII.
- By encrypting PII, individuals can be shielded from damaged credit and identity theft, and an organization can be protected from lost revenue or reputational damage.
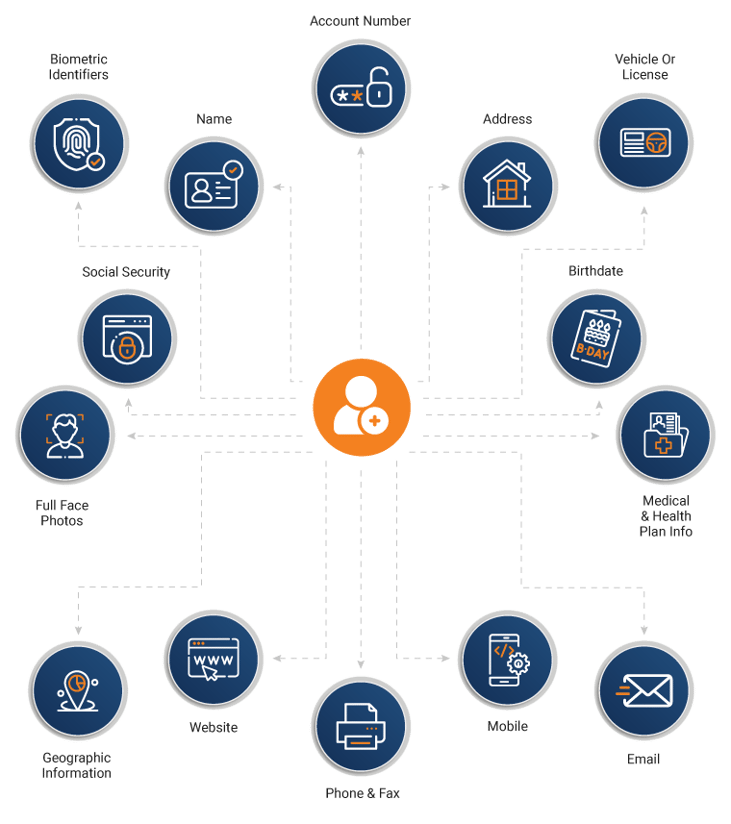
What is Considered PII?
The following items are considered as PII, because they can identify a human being:
.png?width=250&height=184&name=What-is-Considered-PII-(Icon).png)
Sensitive PII:
- Name: Full name, maiden name.
- Address information: (House address, work address or email address).
- Personal identification number: (Passport number, license number, taxpayer identification number).
- Financial information (Account number or credit card number).
- Healthcare information: Medical Records
Non-Sensitive PII
- Race
- Gender
- Place of birth
- Date of birth
- Religious beliefs
- Zip code
- Mobile numbers
- Telephone number on a public register.
Safeguarding Personal Identifiable Information
It is a legal responsibility for protecting PII, ultimately it is the responsibility of the company that controls the PII itself.
The European Union's GDPR went into effect in 2016, it imposed strict rules on what companies doing business in the EU or with EU citizens and confirmed that companies take precautions to protect that data from hackers.
The list of data that the GDPR protects includes:
- Basic identity information(name, address, and ID numbers)
- Health and genetic data
- Racial or ethnic data
- Sexual orientation
- Web data (location, IP, cookie, RFID tags)
- Biometric data
- Political opinions
Some privacy legislation makes it mandatory to have specific individuals in a company designated to have responsibilities in regard to PII. HIPAA requires that companies appoint a specific privacy officer for developing and implementing privacy policies.
Data Privacy Framework Overview

A “Data Privacy Framework” is a conceptual structure that assists businesses in protecting their sensitive data. The framework addresses three main things.
- What data is sensitive
- Analyzing risks associated with sensitive data
- Implementing controls to secure sensitive data
Some established data privacy frameworks are:
- Payment Card Industry Data Security Standard (PCI DSS)
- ISO 27000 family of standards
- EU General Data Protection Regulation (GDPR)
However, one can also create a framework to suit your company's specific needs.
PII Security Controls
Below are some PII security controls that can be used to safeguard PII:
-
Change Management
Keeping a track of changes to the IT infrastructure adding/removing user accounts.
-
Data Loss Prevention
Monitoring incoming and outgoing data to spot any potential data breach.
-
Risk Assessment
Ensure there is a Privacy Impact Assessment (PIA) to get a sense of each type or classification or PII, to know how it is collected, where it is stored, and how it is disposed of, also, the security risks associated with each type of PII.
-
Data Masking
Ensure the data is sent with minimum required information to maintain a level of privacy even if a security breach takes place.
-
Privileged User Monitoring
Logging and monitoring all privileged access to files and databases, users and new permission groups, blocking and notifying when any suspicious activity is detected.
-
Sensitive Data Access Auditing
Audit all access to sensitive data, and send out notifications on detecting any suspicious or anomalous activity.
-
Secure Audit Trail Archiving
Keeping log of all PII incidents and information for a minimum period of 1-7 years, for legal or compliance purposes, and to enable forensic investigation in case of any security incident.
-
User Rights Management
Removing unwanted, unused and misused user accounts that have not been used for several months.
-
User Tracking
Track online user activities, while using official hardware to detect any leak of sensitive data.
-
Ethical Walls
Only release information to the right group of users with minimal required information to maintain data privacy and security.
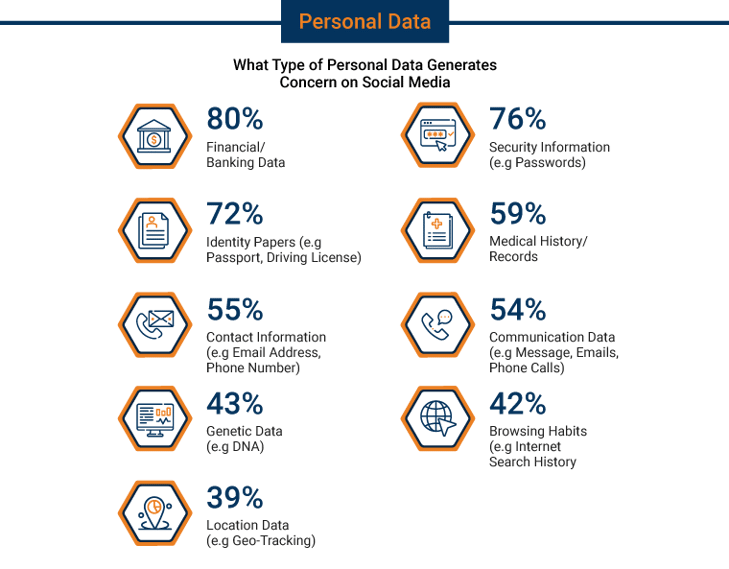
PII Breach Types
Following are the type of data exposed in every PII breach:
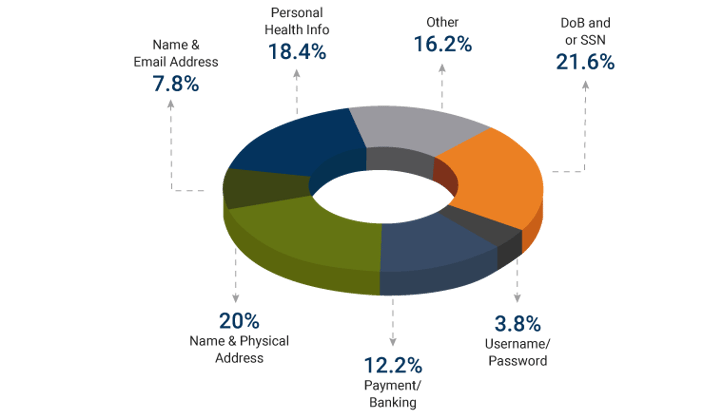
According to the research, PII is the most targeted data for breaches, comprising 97% of all breaches.
QASource Best Practices
- Classify Your PII: Ensure you know exactly what data you have and where it is stored. It will help in implementing the right security strategies for different types of data.
- Perform Risk Assessments: It helps you identify and prioritize your vulnerabilities, so that important issues are addressed first.
- Create the Right Access and Privilege Model: A role-based access model helps you assign certain access levels to sensitive data to protect against improper data loss.
- Use Encryption: Helps in keeping data safe even if it falls into the wrong hands.
- Don’t Store PII You Don’t Need: Implement policy for destroying records securely when they are no longer needed.
Conclusion
Loss of PII can result in harm to an individual in the form of identity theft or other fraudulent use of the information, however we can prevent PII security breaches if we implement the PII security controls. PII security is an extremely critical aspect of any application, which needs to be implemented & tested carefully. At QASource we help reduce the number of PII data security breaches, we embrace security for PII so that issues can be addressed preemptively. To know more, contact QASource experts now.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com



