A Session management vulnerability arises when the tokens used to identify sessions need to be securely stored, appropriately expired, or created using poor algorithms. Read this expert series to know how QASource can help.
Covid-19 has reshaped our life, and so does our work. Remote working has become a significant part of our daily lives now, which has led to a sharp increase in cyber-attacks.
Cost of various Data Breaches in 2021 (Measured in US$ millions)
As per a study done by IBM, the average cost of a data breach is $4.24m. It is a 10% increase in the total cost of a breach compared to last year. The study also highlights compromised credentials as an initial attack vector accounted for 20% of the total breaches in 2021, followed by 17% of phishing attacks.
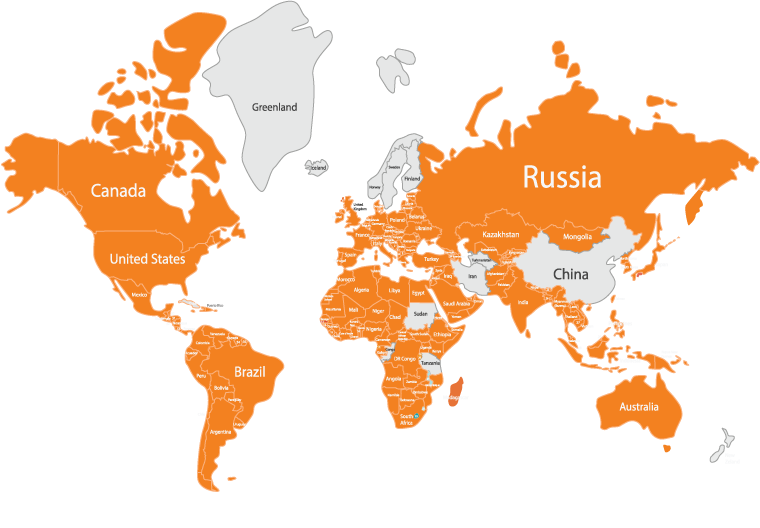
In 2021, Facebook took a massive hit due to session hijacking vulnerability via an android Trojan named Flytrap. The worst part was that it spread across 140 countries.
It primarily attacked the user’s social profile by hijacking Facebook ID, IP address, cookies & tokens, location, and email addresses.
Countries Experienced Session Hijacking Vulnerability Issue in 2021
Vulnerabilities Category in Session Management
There are mainly two categories in which session management vulnerabilities fall:
-
Generating weak session management tokens: This includes creating meaningful, predictable, or encrypted tokens that can be easily cracked as they usually depict a structure. Once the attacker understands the logic for the token generation, he can easily create a valid one using the exposed logic.
-

Insecure handling of session management throughout life-cycle: This includes leaked tokens on the network or logs, session termination not appropriately implemented, token hijacking through other attacks like XSS, and loose cookie scope.
Vulnerabilities & Their Solution in Session Management
Let us discuss about session management vulnerabilities and their solution in detail:
1. Vulnerability: Meaningful tokens
Some developers make the mistake of choosing users' info in a transformed way. For example, it could be a username, user id or email address.
The transformed token may look extremely secure long string. But, if taken a closer look, it could be just a hex value. On decoding, it may reveal the actual value being used for the session id.
For example, Session ID: 757365723d616b3b6170703d746573743b646174653d31372f30352f32303232
When decoded this hex string it will reveal user=ak;app=test;date=17/05/2022
Try decoding the token value using commonly encoding methods like base64 and Hexadecimal to test if it exposes the recipe for the session ID token.
Solution: Avoid using meaningful tokens as a session ID.
2. Vulnerability: Predictable tokens
These types of session-id tokens don't usually have any user-specific meaningful data. However, they consist of a pattern or a sequence that hackers can exploit to guess the valid tokens.
Methods used to generate predictable tokens:
- Concealed sequences: It may be hard to guess when analyzed in its raw form, but they consist of a pattern that gets revealed when decoded. The actual value is passed through multiple patterns.
- Time Dependency: This is quite a common method used to generate session id tokens. A hacker can get his hands on a large scale user tokens in the application due to insufficient entropy implemented in the algorithm for generating tokens.
Solution: Avoid using a predictable tokens generation method for the session ID. If used, it needs to be implemented carefully.
3. Vulnerability: Encrypted Tokens
This method of generating session-id has already proven to be quite vulnerable in real-world apps. It is easy to get attacked.
Below are examples of most common algorithms used by developers to generate tokens.
- EBC Ciphers: Applications with these types of session-id use a token generated by such symmetric encryption algorithm which can be easily decrypted to reveal its content. These tokens may appear quite random & might pass all standard tests for their randomness.
68BAC980742B9EF80A27CBBBC0618E3876FF3D6C6E6A7B9CB8FCA486F9E11922776F0307
329140AABD223F003A8309DDB6B970C47BA2E249A0670592D74BCD07D51A3E150EFC2E69
885A5C8131E4210F
But this algorithm operates on an 8/16 byte block of data & converts to the cipher-text as displayed below.
rnd=2458 68BAC980742B9EF8
992;app= 0A27CBBBC0618E38
iTradeEU 76FF3D6C6E6A7B9C
R_1;uid= B8FCA486F9E11922
218;user 776F0307329140AA
name=daf BD223F003A8309DD
ydd;time B6B970C47BA2E249
=6344304 A0670592D74BCD07
23694715 D51A3E150EFC2E69
000; 885A5C8131E4210F
Solution: Avoid using these weak/vulnerable algorithms to generate tokens as a session ID.
4. Vulnerability: Disclosure of tokens on the network or logs
This becomes a concern when session-id transmits through an unsecured network which hackers can easily sniff to get their hands on session tokens.
Also, there could be some cases where the session-id token is exchanged via HTTP instead of HTTPS. For example, most applications use HTTP to load static content like images, CSS, and scripts.
Also, logs need to be monitored for session tokens, user browser logs, web server logs, or ISP proxy server logs.
Hackers can simply sniff the session token value & decrypt it to reveal its original form.
Solution: Avoid using switching HTTPS → HTTP, or keep eye logs at various levels, like browser, web application & ISP logs.
5. Vulnerability: Session Termination not Appropriately Implemented
If session time is not limited it can give a hacker an ample amount of time to find/exploit the session token key.
Secondly, a few scenarios need to be covered, like session expiring on logout, inactivity, or closing the browser.
Solution: Implement a shorter period of session time & expire session keys when a user logs out or closes the browser.
6. Vulnerability: Stealing Tokens Through Other Attacks like XSS, CSRF & Malware
If the application is vulnerable to other attacks like those discussed above, it could cause hijacking of the session via stealing the cookies, local storage, or session-related data.
It is the most common method used for stealing the session data. Phishing attacks almost accounted for 17 percent of attacks in 2021, which uses these vulnerabilities to attack the victim.
Solution: The application needs to test for the other vulnerabilities. If found, we need to fix them to avoid further exploitation.
7. Vulnerability: Loose Cookie Scope
Session management can be implemented through a number of different methods like cookies, hidden form fields, SSL & URL rewriting. But the most common one is through cookies. Cookies are helpful in many ways, but they can also be dangerous if they get into the wrong hands.
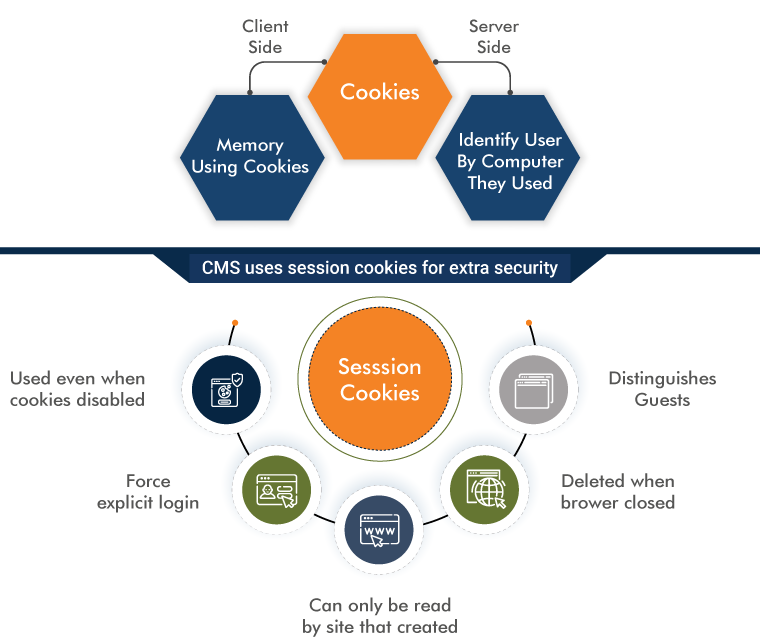
Solution: Keep the cookie's scope as limited as possible. If there is a need to be shared across other domains, keep it secure. Try avoiding sharing with insecure third-party application.
Types of Session Hijacking Attacks

Types of Session Hijacking
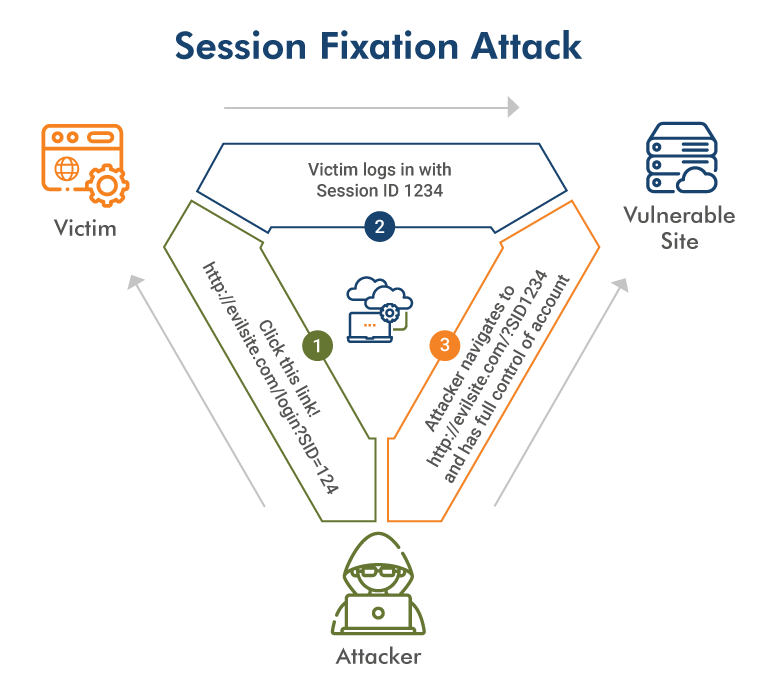
Session Fixation
The attacker already has a valid session ID key & forces the target user to log in utilizing the hacker-provided session ID. There are multiple ways to perform this attack, for example, an HTTP query to pass the session ID.
Session Prediction
A session ID should be distinctive and difficult to speculate. Not all developers use recognized libraries provided by the frameworks. Developers produce custom session IDs and end up with insecure implementation.
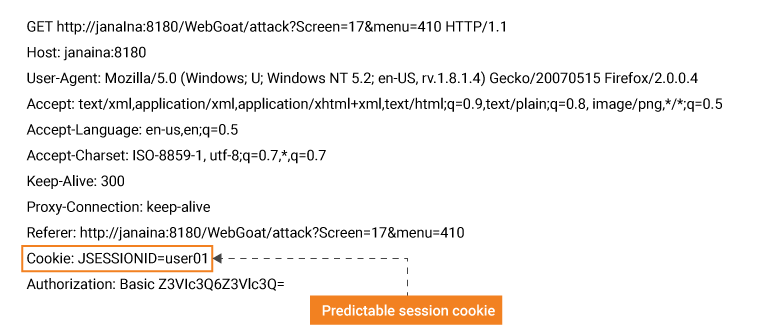
For example, here, the JSESSIONID token uses a user-id parameter as its value which is quite easily predictable.
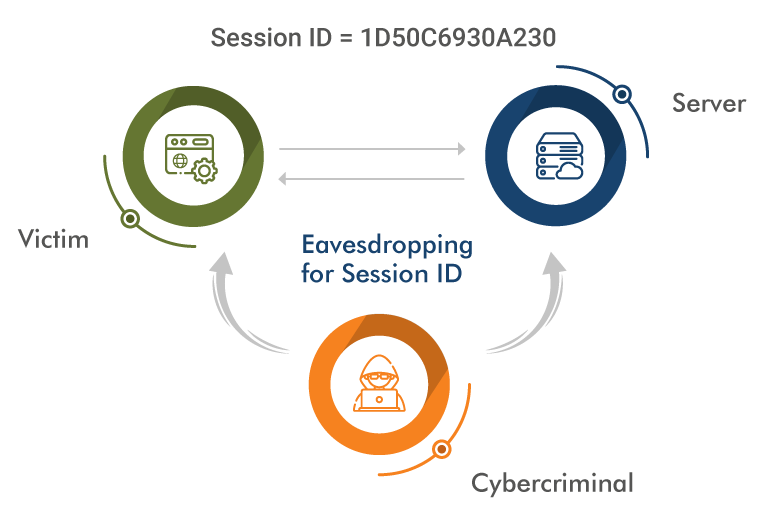
Session Side-Jacking
Side-jacking is accomplished through sniffing. The hacker could easily get involved in the transmission between the client & server if the client is utilizing the unsecured network.
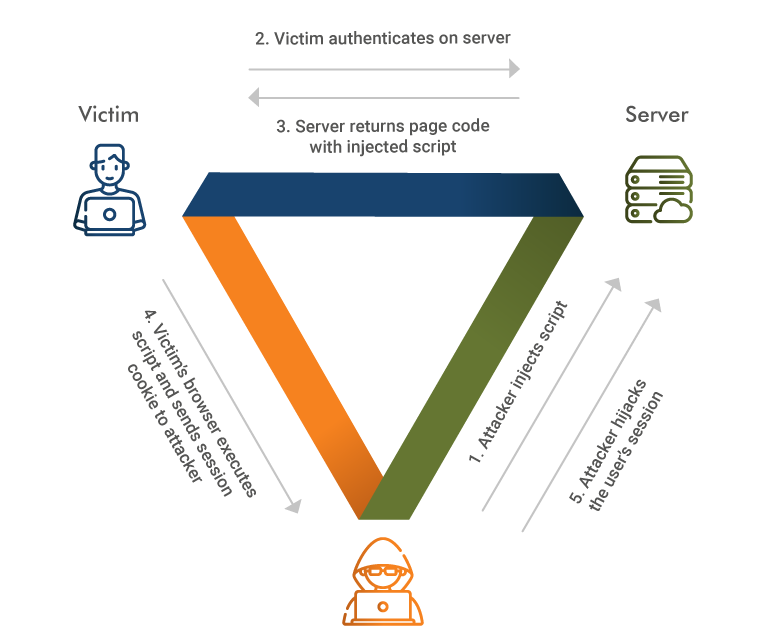
Cross-site Scripting(XSS)
Stealing a session ID through XSS is likely the most common attack, which uses JavaScript code to read the cookies & deliver them to the hacker. Similarly, users can also use the malicious malware to inject the code, read the cookies, or access the local storage files.
Best Practices for Session Management
According to the OWASP guidelines, following are the best practices for session security:

- Selection of good algorithms to generate the session identifiers as they should not be easy to guess via brute force. It must be random with good entropy.
- Terminating session when user logs out or closes browser.
- Using trusted servers to generate the session identifiers.
- Periodic timeout implementation of sessions.
- Prevent unauthorized users access to the server side session data via proper access control implemented.
Session Security Testing Tools
There are many aspects that must be examined when we are testing for the security of the session management for an application. Manual testing of the session token can take forever, so we have numerous tools available in the market.
Below are the most popular tools to test for session security:
Zap
Zap tool supports testing for various types of session management, like cookie-based sessions, script-based, and HTTP authentication methods.
Burp Suite
The Burp Suite also has inbuilt capabilities like the sequencer feature that is used to test for the session management with detailed reporting.
Conclusion
The session management mechanism is vulnerable to a wide range of attacks. Hackers keep searching for loopholes in applications session management to hijack the session & masquerade that user to carry out unauthorized actions.

Securing session management tips:
- Generate Large, Random & Strong tokens
- Secure tokens throughout their lifespan
- Properly log, Monitor & alert for brute force attacks
Session management is an extremely critical aspect of any application, which needs to be implemented & tested carefully. At QASource, we have expertise in the security testing domain in order to make sure our client's businesses remain thriving & secure.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com



