Today, APIs have grown large in numbers and have become a necessary part of software development. It is, therefore, crucial to adopt an extensive API testing strategy to ensure that the application interacts well with all APIs.
API security is nothing but building APIs in such a way that attackers can’t exploit them and their vulnerabilities. API security is a key component of modern web application security. Commonly found vulnerabilities in APIs include broken authentication and authorization, lack of rate-limiting, and code injection. There are the best API security testing tools available in the market, including APIsec and Postman. Before knowing how to do API security testing, we need to understand that a vulnerable API could lead to:

- Unauthorized Access
- Data Leakage
- Sanctioning Fuzzy Input
- Injection Vulnerabilities
- Parameter Tampering
API Security Attacks and Trends
- A Salt Labs report reveals an extraordinary surge in attacks on APIs in the first half of 2021. Monthly API call rates increased by 141%, whereas malicious traffic increased by a gigantic 348%.
- 94% of respondents of the Salt Security Survey have experienced an API security breach incident in 2020.
Common Security Problems Found in Production APIs
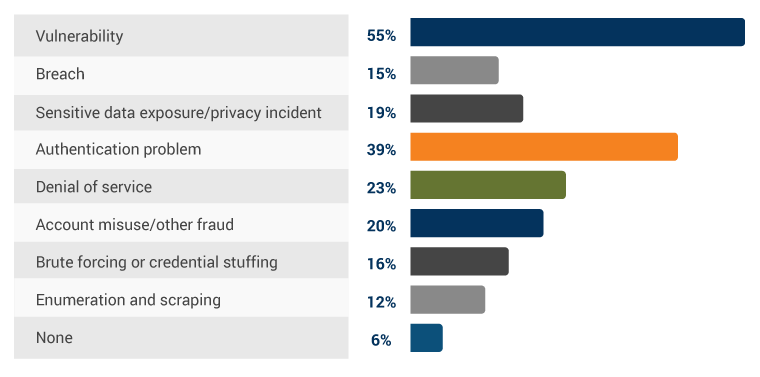
- Salt Labs states that 62% of organizations have very basic or no strategy in place for API security which is concerning.
- In the year 2019, Airtel API was found leaking the information of their customers by using their numbers. It affected around 325 million users of Airtel.
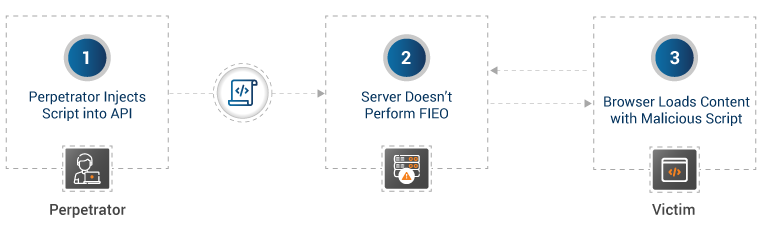
- In 2019, a bug CVE-2019-5786 was found in the File Reader API. Almost, all major browsers were impacted by this, and hackers exploited it wildly to target Chrome users.
Top 10 API Security Issues
Broken Object Level Authorization
Every API function should have object-level authorization checks that access a data source using input from a user
Broken User Authentication
Incorrect implementation of authentication mechanisms in API allows attackers to compromise authentication tokens or implementation flaws
Excessive Data Exposure
Most developers look for generic implementations in API and are likely to expose all object properties without considering their sensitivity
Lack of Resources and Rate Limiting
Mostly, APIs do not impose any restrictions on the size or number of resources that can be requested by the client/user. It can result in low server performance, leading to denial of service (DoS) attacks
Broken Function Level Authorization
Sometimes APIs tend to have an unclear separation between administrative and regular functions that lead to authorization flaws
Mass Assignment
The binding client-provided data (e.g., JSON) to data models, with improper filtering of properties based on an, allow list, leads to mass assignment
Security Misconfiguration
Security misconfiguration is due to misconfigured HTTP headers, open cloud storage, unnecessary HTTP methods, and error messages containing sensitive information
Injection
Injection flaws include command injection, SQL injection, etc. The attacker’s malicious data can force the interpreter to execute any script or command to access data without proper authorization
Improper Assets Management
To mitigate APIs' security issues, they should be properly managed hosts and deployed API versions inventory
Insufficient Logging and Monitoring
Insufficient logging and monitoring can encourage attackers to attack systems that may allow them to tamper with, extract, or destroy data
API Security Testing Methods
Input Fuzzing
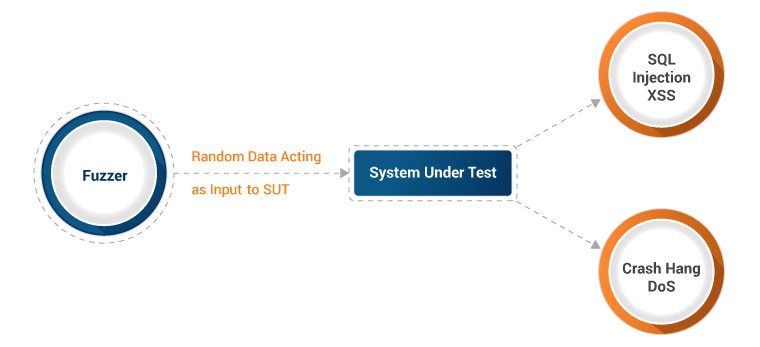
Command Injection
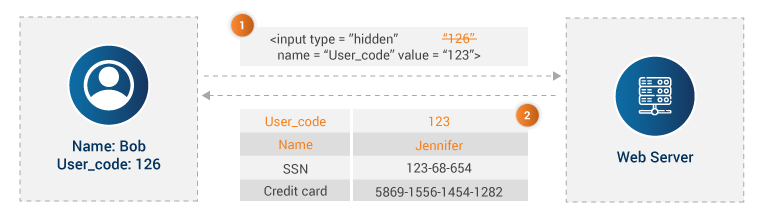
Parameter Tampering
Test Unhandled HTTP Methods

API Security Best Practices
Some of the most common ways by which you can ensure API security include:
-

1. Access Control
Authenticating API traffic using OAuth and JWT allows you to set access control rules to specific API resources.
-

2. Encryption
Encrypting data using TLS is standard practice for API security. Decrypting or modifying data would require users to provide a valid signature.
-

3. Vulnerability Assessment
It is important to run penetration tests on your APIs so that vulnerabilities are caught at the right time.
-

4. Quotas and Throttling for APIs
If quotas for API are defined regarding how many times it can be called and tracking its usage over time, it can help you keep them secured. It can reduce the chances of DoS attacks.
-

5. Partner With an API Testing Services Provider
Partner with a provider that can place a strong API security testing process, like QASource. The professional QA engineers at QASource can implement automated testing techniques to increase the efficiency and comprehension of API tests.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com



