
Every service-based organization now places a high priority on cybersecurity, as any security loophole can be used as an easy target for malicious attacks. Therefore, concentrating on thorough security testing procedures is the best strategy to secure sensitive data. The major reason network penetration tests are important for an organization's security is that they teach staff how to deal with any form of malicious entity break-in. To find risk factors connected to crucial cybersecurity implementation projects, network penetration testing is necessary. Even though doing penetration tests on a regular basis is important, many people outside of the cybersecurity industry are unaware of its importance.
What Is Network Penetration Testing?

Network penetration testing is an attempt to breach an organization’s network, with the objective of identifying security weaknesses in the network. Modern networks are extremely complex, with a combination of WAN/LAN, servers, workstations, IoT devices, and security technologies like firewalls. The weak link among these will allow attackers to penetrate the network.
Types of Network Penetration Testing
Each kind of penetration test has a different set of skills, procedures, and resources that must be used, and it should be in line with a particular business objective. The types of network penetration testing services that must be performed while evaluating software products are:

-
Internal Network Penetration Testing: Internal network penetration testing is performed to detect what an attacker could achieve with initial access to a network. It can mirror insider threats, such as employees intentionally or unintentionally performing malicious actions.
-

External Network Penetration Testing: An external network penetration testing is designed to test the effectiveness of perimeter security controls to prevent and detect attacks, identifying weaknesses in internet-facing assets like web, mail, and FTP servers.
Vulnerability Trends
Based on a survey, the most common cyber attacks experienced by US companies are of the following kinds:
Source: BakerHosteler,2020
As per the study, it comes as no surprise that people and organizations are worried about potential hacking situations and information breaches. Other than revenue losses, such varieties of cyber attacks will result in a bad reputation and will subject businesses to strict government rules and expensive settlements.
Network Vulnerabilities
A network vulnerability is a flaw or weakness in organizational procedures, hardware, or software that, if exploited by a threat, could lead to a security breach. The image below shows some network vulnerabilities:
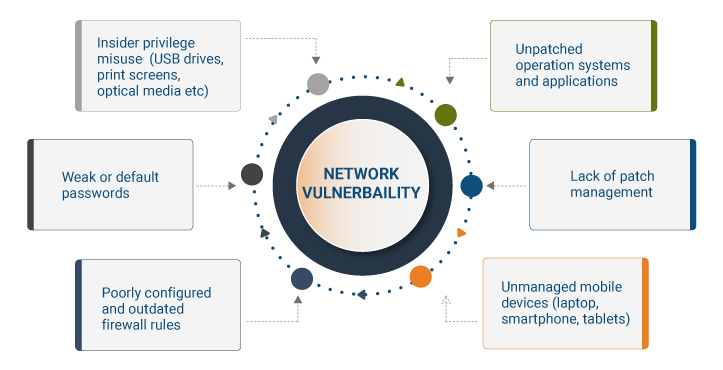
Types of "Network Security Threats"
If your business is aware of the threat described below, you can develop more thorough policies and procedures to protect your organization’s data security.

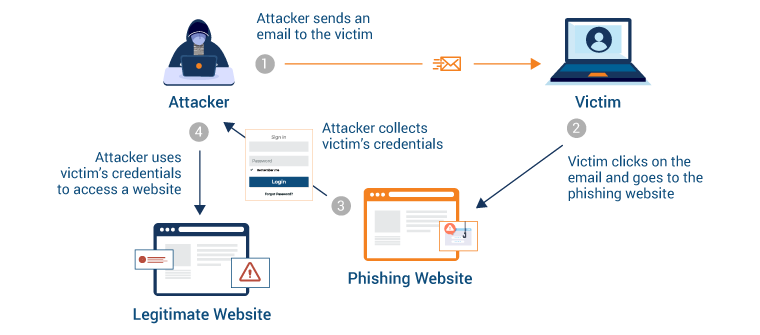
Phishing
Phishing is a trick in which attackers pretend to be someone that they are not in an attempt to steal information. This is often communicated through an email or message.
Malware
Malware is malicious software that is created to steal sensitive data, and files, or compromise and damage working systems.
Source: www.av-test.org
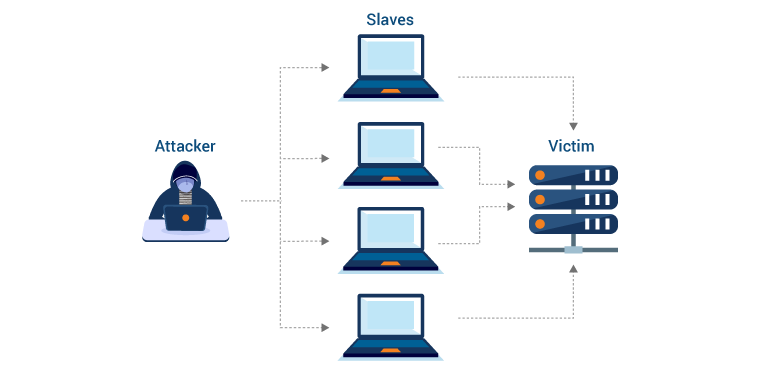
DDoS attack
Multiple infected computers attacking one target to prevent service from being provided to the system's legitimate users is known as a DDoS attack, and it can target any network resources.
DNS Attack
A DNS attack is an exploit that could allow an attacker to penetrate through domain name system (DNS) vulnerabilities, meaning it would route the communication to a website based on the hacker's exploit.
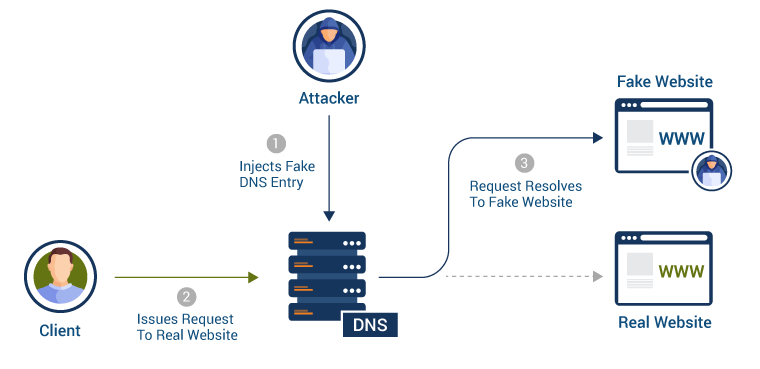
Advanced Persistent Threats
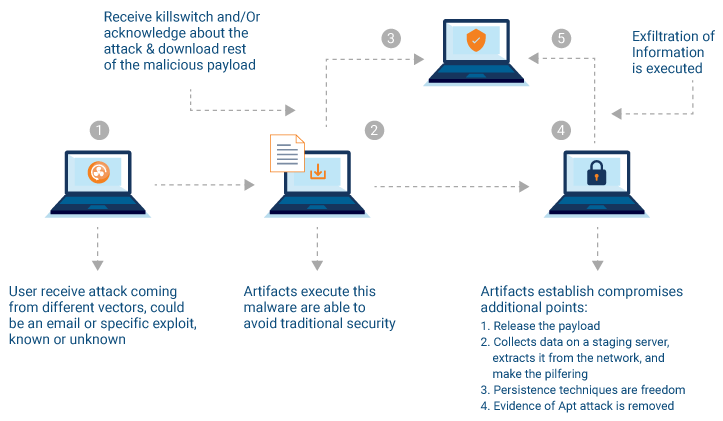
An APT is a certain type of cyber attack that allows an intruder to gain access to a network and remain undetected for a long period of time.
Importance of Network Penetration Testing
Be it startups, mid-market, or enterprises, it is critical for organizations of any size to do penetration testing on their systems and infrastructure to make sure that there are no security breaches that might cause harm to reputation or revenue loss. Listed below are some of the most important factors why penetration testing matters:
-
Real-time Experience
Penetration tests should be done in order to learn if the security controls you have in place actually work. Pentest gives you real-time experience in dealing with an attack.
-
Risk Prioritization
Network security penetration testing helps in detecting what vulnerabilities lie in your network. Without prioritization, we can not check which of these vulnerabilities to patch first.
-
Uncover Vulnerabilities
Pentest is done to uncover loopholes in your network. Penetration testing does whatever possible to breach your network in a similar manner as a hacker.
-
Determine Attack Vector Feasibility
Penetration testing vendors enable security staff to effectively identify and respond to various forms of cyber attacks
Network Security Testing Tools
The best network security testing tools give you a complete picture of your network's security state. Below are the most popular tools to test for session security.

-
Wireshark
-
Wireshark is an open-source tool that is used to capture and interpret network packets. The tool is available for various systems, including Windows, Solaris, FreeBSD, and Linux.
-
-
Aircrack
-
Aircrack is an open-source tool that is used for cracking flaws within wireless connections by analyzing data packets for an effective protocol for exporting text files for analysis.
-
Best Practices for Network Security
As a variety of useful network penetration testing tools are available, system scanning services can be completed quickly and with older, more convenient services. Let us take a look at how you can secure your network from a security breach:
Conclusion
A network vulnerability is a weakness or flaw in the software, hardware, or organizational processes, which when compromised by a threat, can result in a security breach. Network security is an extremely critical aspect of any application, which needs to be implemented and tested carefully. At QASource, we provide network penetration testing services and we have expertise in the security testing domain in order to make sure our client's businesses remain thriving & secure. Request a free quote to implement cutting-edge network penetration testing services for software products.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com


