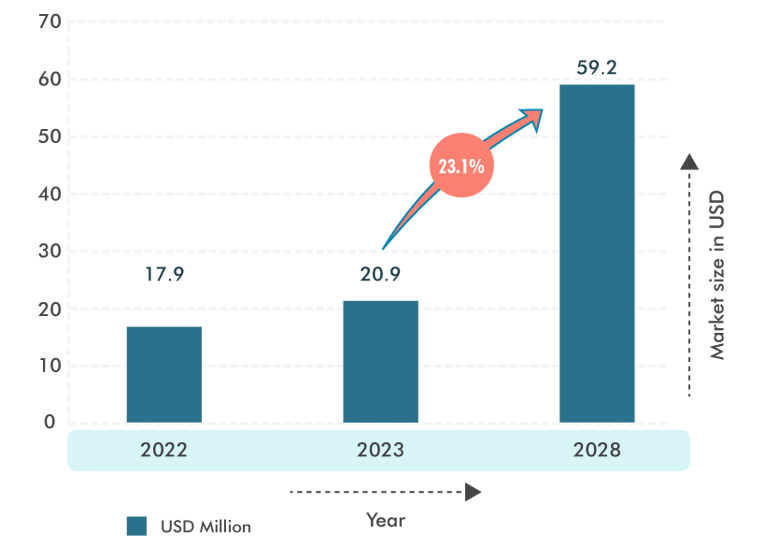
In an era dominated by Internet of Things (IoT) devices, safeguarding the integrity and security of the data and services they handle is no longer a mere consideration; it's paramount. It is evidenced through the future projection that the IoT market size will grow from USD 20.9 bn to USD 59.2 bn by 2028 at a CAGR of 23.1%.
This blog aims to shed light on the IoT security assessment, delving into the complexities of IoT architectures and navigating through the diverse networking layers and associated components and protocols.
Our journey doesn't stop at mere exploration; we delve into exposing vulnerabilities and assessing their impact. We emphasize strategies that go beyond mere mitigation, aiming to strengthen the very foundation of IoT security.
Understanding the IoT Security Landscape
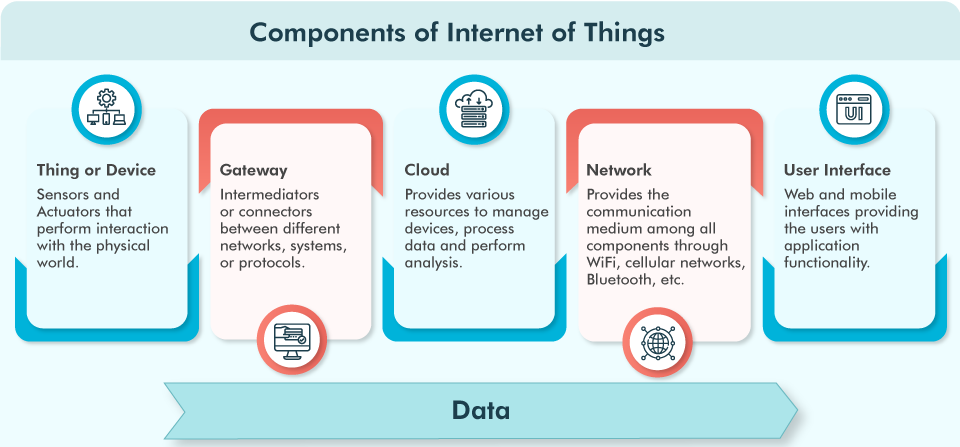
An IoT (Internet of Things) ecosystem comprises various components that enable communication, data exchange, and automation. These components can be classified into several categories based on their functions and roles within the IoT security landscape:
Why IoT Security Assessment is Important?
Imagine your smart devices, like thermostats, cameras and lights all talking to each other over the internet. Now, what if we don't make sure they're protected?
In essence, security testing in IoT is not merely a precautionary measure but a proactive strategy to address the multifaceted challenges that arise from the interconnected nature of IoT ecosystems. It plays a pivotal role in upholding IoT networks' integrity, reliability, and privacy, thereby safeguarding user trust and mitigating the risk of widespread cyber threats.
Some challenges if the IoT system is hacked:
- Exposure of User Data: Unauthorized access to sensitive records stored within the IoT infrastructure compromises user privacy and confidentiality.
- DDoS Attacks and Network Congestion: The real-time execution of distributed Denial of Service (DDoS) attacks, leveraging compromised IoT devices as integral components of botnets. This malicious activity can result in immediate network congestion or the unavailability of essential online services, severely disrupting normal operations.
- Device Manipulation and Malfunction: Malicious activities manipulate or induce malfunctions in IoT devices, impacting critical operations. This could have far-reaching consequences, especially in sectors where IoT is integral to infrastructure and operational efficiency.
IoT Security Assessment Checklist to Follow
With the diverse range of IoT components exchanging sensitive data over the internet, it becomes critical to prioritize the security of an IoT ecosystem. This IoT security assessment checklist is a comprehensive guide for conducting thorough security testing on IoT systems.

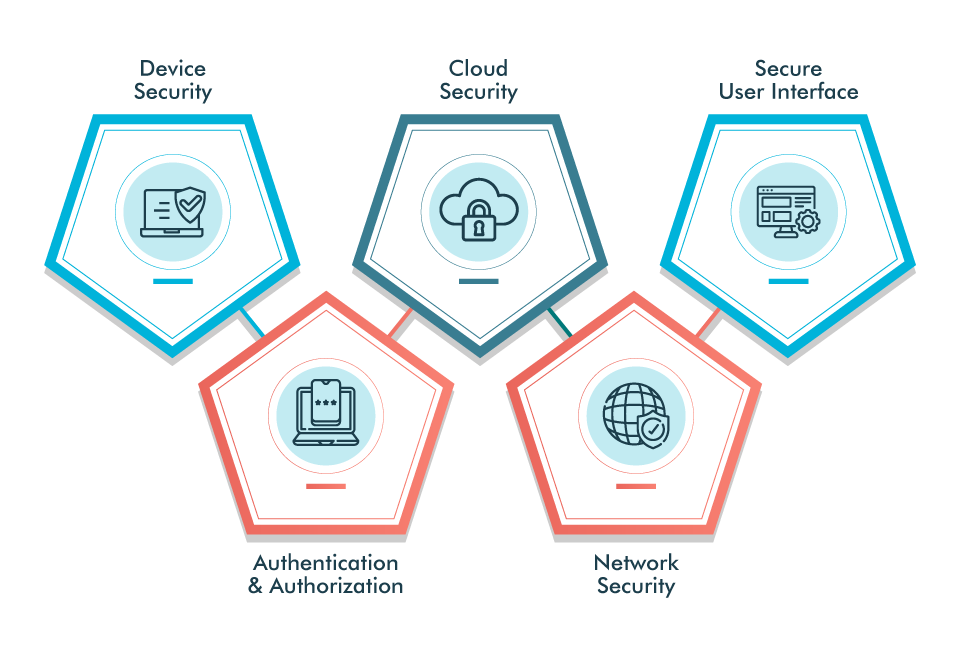
- Step 1. Device Security: Regular updates and patch management are needed to address vulnerabilities and safeguard devices from physical tampering.
- Step 2. Authentication and Authorization: Ensuring that only authorized entities can access and control IoT infrastructure.
- Step 3. Cloud Security: Ensuring that the cloud infrastructure and the involved services have implemented the necessary security measures to avoid malicious attacks.
- Step 4. Network Security: Securing the communication channels between devices and the IoT platform and ensuring privacy by protecting sensitive user data collected by IoT devices.
- Step 5. Data Encryption: Protecting data as it is transmitted between devices and stored on IoT platforms by configuring robust encryption mechanisms.
- Step 6. Secure User Interface: The involved web and mobile interfaces should implement the necessary security standards per the web and mobile security best practices to avoid exposure to sensitive data.
In addition to the considerations mentioned earlier, a critical aspect of ensuring the security of an IoT ecosystem is the evaluation of the communication protocols used among the diverse IoT devices and components. These protocols may introduce vulnerabilities into the IoT system by their very design. Moreover, multiple protocols are typically employed to facilitate data communication across various TCP/IP network layers, further highlighting the need for a thorough IoT security assessment framework.
Below are the most widely used protocols at each TCP/IP layer.
Application Layer
- HTTP
- MQTT
- AMQP
- CoAP
- DDS
Transport Layer
- TCP
- UDP
Network Layer
- IPv4
- IPv6
- ZigBee
Physical/Data Link Layer
- WiFi
- BLE (Bluetooth Low Energy)
- IEEE 802.15.4
Diverse Tools and Utilities for the IoT Testing Landscape
Every IoT system is inherently unique, shaped by the distinctive components that address specific challenges in diverse domains such as healthcare, government, logistics, and more. Given this complexity, creating a one-size-fits-all list of tools capable of comprehensively testing the security of an entire IoT ecosystem proves challenging. Instead, a synergistic approach involving distinct tools is necessary to conduct a thorough security assessment.
However, QASource has developed proprietary utilities designed to uncover security weaknesses within an IoT system. These in-house utilities analyze the various IoT components involved, and the dedicated security team at QASource consistently maintains them, keeping these utilities up-to-date with the latest known vulnerabilities.
IoT Security Assessment Best Practices
Here are some best practices for conducting security testing in IoT:
- Ensure a strong authentication and authorization process for devices
- Ensure the physical security of IoT devices
- Encrypt network data in transit and at rest
- Setup monitoring and anomoly detection systems
- Keep IoT devices, firmware, and software up to date
- Ensure a proper firewall is setup for network services

- Implement a device management solution
- Ensure security for user interface endpoints of the IoT system
- Segment IoT networks from critical infrastructure
- Implement zero-trust security model
- Validate and sanitize IoT data inputs to prevent injection attacks
- Conduct regular security audits and vulnerability assessments
How QASource Can Help?
At QASource, our team has the proficiency to meet the above challenge, ensuring that client data and infrastructure are secure from the malicious activities of bad actors. Connect with our experts to protect your IoT-based system against evolving cyber threats. Your security is our priority; let's build a resilient IoT ecosystem together. Take the first step towards a secure future; contact us now!

Conclusion
Cybersecurity stands as a pivotal pillar in the realm of IoT ecosystems. The risks associated with neglecting IoT security are profound, ranging from data breaches and privacy violations to compromised critical infrastructure, damage to brand reputation, and potential legal repercussions. Navigating the challenges outlined above demands a diversified IoT security assessment framework. This allows the team to conduct thorough and realistic security assessments across various IoT protocols, computing environments, data storage, and encryption mechanisms.



