A cloud security assessment is a complete evaluation of hosted application as well as the platform itself. In this expert series, we talk about how can we do that along with some highlights from the RSA conference and GDPR.
RSA Conference 2018 Highlights
We attended the RSA Conference 2018 to support our customers who were exhibiting in the security domain.
RSA 2018 was an inspiring opportunity to meet other security professionals and learn from each other. The conference was full of actionable intelligence on how to combat security breaches and avert costly information security scenarios, not to mention the information on thousands of tools, solutions, and technologies.

Key Takeaways
-
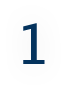
New attack techniques uncovered
- Repositories and cloud storage data leakage
- Hardware vulnerabilities like Meltdown and Spectre
- Cryptocoin mining
- Big data analytics, de-anonymization, and correlation
- Exploitability in ICS/SCADA
-

Upcoming innovative security products
-
Gave an overview of what's coming next in security. For details refer to: https://www.rsaconference.com/library/blog/this-years-innovation-sandbox-theme-taking-humans-out-of-the-security-equation
-
GDPR
This is the biggest development in years for data privacy regulations. GDPR stands for General Data Protection Regulation, which is now applicable in regard to all EU citizens. Under this new set of regulations, all organizations must protect the personal data and privacy of EU citizens.

What to verify in Cloud Security
Deployment Model
Firewalls and intrusion detection systems must be in place to secure cloud environment.
Techniques: Server Hardening, Firewall, Router, DNS, and Mail Server Testing
Data Security
As in cloud model, enterprise data is stored outside its boundary, verify security checks like data encryption and authorization to control data access.
Techniques: XSS, Access Control Weakness, OS/SQL Injection Flaws, CSRF, Cookie Manipulation, Hidden Field Manipulation, Insecure Storage, and Insecure Configuration
Network Security
Verify network for security against MITM attacks, IP Spoofing, Port Scanning, Packet Sniffing etc. Network traffic must be encrypted using techniques such as SSL/TLS.
Techniques: Network Penetration and Insecure SSL trust configuration
Regulatory Compliance
Confirm adherence to regulatory and industry standards such as ISO, SOX, HIPAA, PCI etc.
Data Privacy
As on cloud data stores are shared across multiple enterprises, so tests to ensure that data of an application is not accessible to other applications are must to execute.
Techniques: Encrypted data stores
Disaster Recovery and Availability
In case of attack, check if the application is still available to customers. Multi-tier architecture, load balancing approach, business continuity, and disaster recovery techniques need to be verified.
Techniques: DOS Attacks
Identity Management [IdM] and Sign-on Process
Verify the security of IdM model of cloud vendor.
Techniques: Session management weaknesses and Authentication weakness
Evaluation – Tools and Technologies
Tenable.io Vulnerability Management
Tenable.io Vulnerability Management is the solution for ensuring security of data on cloud. It is a widely used tool for cloud security assessment.
This tool works with Microsoft Azure, Salesforce, Rackspace, and AWS but does not support Google Cloud Platform.
Some of the crucial checks at application and cloud environment level.

-
Application
- Rogue authentication, unauthorized user access
- Unauthorized database access (sql injection)
- HTTP header injection
- Fake encryption check
- Is device information available (like OS, etc)
- Can device be used as a host for malicious activities
- Rogue ftp/api access
- phpmyadmin vulnerabilities
- Rogue cookies use
-
Cloud
- Compromised SSL security - self-signed/old certificates, weak ciphers
- Secured data visibility in public network, anonymous ftp enabled, https not used, sql injection
- How well the network is protected, wrt to routers, data-packets, encryption protocols
- Are the various user rights properly working
- Identify how well the virtual machines isolate your workload
For detailed information refer: https://www.tenable.com/products/tenable-io/vulnerability-management
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com


