Don’t let your application security fall flat. In this version of the expert series, let’s discuss the important application security trends in 2020 so that you are prepared for security threats that may come your way.
Application Security Trends
2020 and the difficulties it has presented has drove developers and users alike to depend on new and evolving technologies. Telehealth and eLearning are two of the fastest growing industries in the world, but are also common targets for security hackers. In our latest version of our expert series, we'll go over cybersecurity risks the pandemic unlocked and discuss the recent trends in network and application security.

Security Attacks Examples
About 130 Twitter Accounts Targeted in a Single Week
A variety of high profile twitter accounts including Joe Biden, Jeff Bezos, and Elon Musk were taken over by hackers.
Colorado City Paid a Heavy Amount as Ransom After Cyberattack
Colorado officials said that hackers disabled the city’s network services and blocked its access until the city paid a ransom. Emails, phones, online payments, and reservation systems were temporarily down.
Summit Medical Associates Disclose Ransomware Attack
The healthcare industry has become a hotspot for hackers during the current pandemic. 51% of total incidents that took place in the first quarter of 2020 were related to healthcare which impacted patients and their private information.
GitHub and GitLab OAuth tokens Were Stolen From Waydev
Github’s security team detected suspicious activity originating from a customer's Waydev token and found a breach. Waydev patched the vulnerability on the same day.
Unacademy Data Breach
22 million users' details were exposed by this data breach on an Indian based online learning platform.
Emerging Threat Areas
-
1. Smart Medical Devices and Electronic Medical Records (EMRs):
As the healthcare industry moves online and telehealth continues to grow, so do the concerns around privacy and cybersecurity. The SEI at Carnegie Mellon University stated that a compromise of patients' data has the potential to affect treatment plans and the dosages provided to a patient.
-

2. Connected Vehicles:
Vehicles infused with IoT generally need a smartphone integration. With the rising number of connected vehicles, we may see an increase in system vulnerabilities. These may include vehicle immobilization, accidents, and stealing of sensitive data.
-

3. eLearning:
As school districts and colleges turn to online learning in the wake of Covid-19, students' private financial and educational information must be guarded more carefully.
-

4. Social Engineering:
Cyber criminals are now taking advantage of human psychology for their attacks. Hackers attempt to access sensitive information by tricking people through phone calls and social media.
-
5. IoT Attacks:
According to Statista, there could be more than 75 billion devices connected to IoT by 2025. These include computers, webcams, and home security systems. Once intruded, IoT devices can create havoc and lock down essential equipment for financial gain.
-

6. Cryptojacking:
Cryptojacking is emerging as one of the most common security threats. Attackers mine the cryptocurrency by hacking third-party computers and steal money by secretly piggybacking on someone else’s systems.
Trends
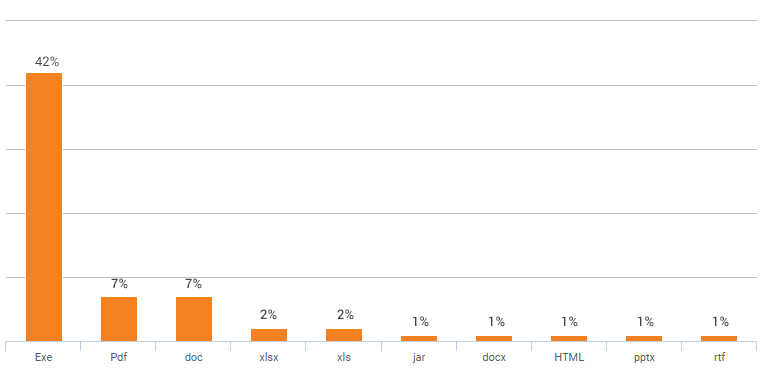
1. A recent report by Check Point show that 42% of malicious files shared through web were exe.
Top Malicious File Types
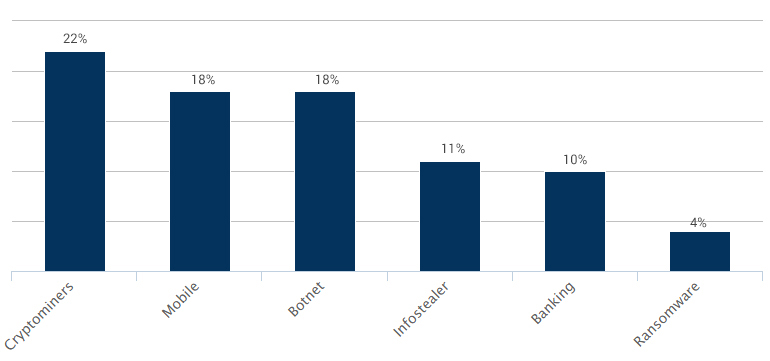
2. The same report reveals that cryptomining topped the security attack charts in the first half of 2020.
Global Cyber Attack Categories
3. Ransomware actors practice double extortion where they hack the victim's data and blackmail them to leak their data if the victim refuses to pay ransom.
Best Security Practices
1. Move to Identity-Level Control
Since we can connect a single IoT device to multiple users, teams should focus on identity-level control instead of device-level control. Teams need to understand how a user is accessing a device to better understand a system's vulnerabilities.
2. Count on Up-To-Date Encryption Protocols
The data which is moving in and out of a system or application should be strongly encrypted. Teams need to produce a strong level of encryption.
3. Understand Your Endpoints
Whenever a new endpoint is introduced to a network, it must go through vigorous security tests to sure up any vulnerabilities.
4. Choose a Security Solutions Partner
Application security is complex and impacts a company’s reputation. Businesses must look for a trusted partner who has high technical expertise and integrity.
5. Vulnerability Scans and Penetration Tests
Perform a vulnerability scan on your application and review the failed areas. A reliable security solutions partner will run penetration tests to exploit any weaknesses.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com



