In today's digital ecosystem, where data velocity and integrity are paramount, the Cloud Speed Layer emerges as a critical component in managing and processing vast amounts of information with minimal latency. This layer, incorporating elements such as Service Bus, Function Apps, and Redis Cache, is pivotal in handling the rapid ingestion and processing of data from various sources, including IoT devices and sensors. It is particularly crucial for applications that demand instantaneous insights and real-time data handling.
However, the efficiency and reliability of the speed layer are only as strong as its security framework. This blog delves into the significance, challenges, and best practices of security in the Cloud Speed Layer.
Significance of Security Testing in Cloud Speed Layer
Security testing within the Cloud Speed Layer holds immense significance due to its critical real-time functionalities. Below are the key points highlighting its importance:
Real-Time Operations
Its real-time operation makes it a prime target for cyber threats. Rigorous security testing is essential to protect sensitive data from these threats.
Data Validation
With the rapid processing and transmission of data, the Speed Layer needs security testing to block unauthorized access and data breaches, thus ensuring the safety of crucial information at high speeds.
Complex Architecture
The layer's complex architecture, comprising interconnected components, requires in-depth security testing to uncover and address vulnerabilities in each component.
Third-Party Services Integration
Considering the Speed Layer's frequent integration with third-party services and APIs, security testing becomes crucial to assess and enhance the security of these integrations.
Protection of Sensitive Information
Security testing is vital to establish strong authentication, authorization, and data encryption protocols. It prevents unauthorized access to sensitive real-time data.
Application Security
It plays a significant role in gauging the Speed Layer's resilience against various cyber attacks, such as denial-of-service and injection attacks. This testing ensures the layer's efficient operation under diverse and challenging conditions.
Regulatory Compliances
Security testing is instrumental in aligning the speed layer with stringent data security standards set by regulatory bodies like GDPR and HIPAA. This alignment is crucial to avoid legal issues and potential damage to reputation.
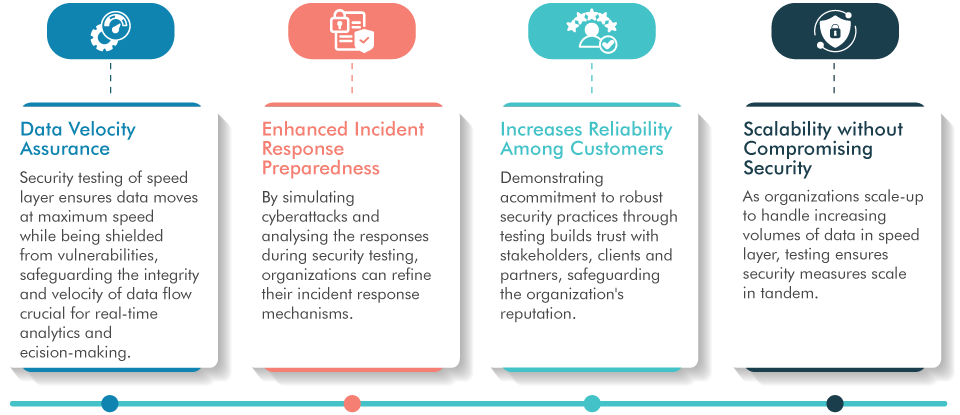
Benefits of Security Testing in Cloud Speed Layer
Security testing offers many benefits and is crucial for maintaining the integrity and efficiency of cloud-based systems. Here are some of them:
Challenges in the Security of Cloud Speed Layer
It faces various security threats, making security testing an indispensable part of maintaining its integrity. Some key challenges underline the need for robust security measures:
- Data Encryption: It's crucial to secure data transmission within the component. Encryption ensures that data remains protected and is not misused or intercepted during transfer.
- Insecure Coding Practices: Poor coding can lead to vulnerabilities like SQL injection and Cross-Site Scripting (XSS). These are often the primary reasons for security breaches in the component.
- Outdated Software: Using outdated software makes it vulnerable to attacks. Hackers often target such weaknesses, making it crucial to keep all software up to date.
- Unauthorized Access: In high-speed environments like the Cloud Speed Layer, preventing unauthorized access is vital. Ensuring robust access controls is crucial in safeguarding against unauthorized entry.
- Insecure APIs: APIs that lack proper security can lead to significant data breaches. Deliverable access control and poor input sanitization must be addressed through penetration testing.
- Insecure Configuration: Incorrectly configuring components within the Speed Layer can expose the system to various attacks. These configurations are regularly reviewed and adjusted to maintain the layer's security.
Addressing these challenges through comprehensive security testing and proactive measures is essential to protect the component from potential threats and vulnerabilities.
Best Practices for Cloud Speed Layer Security Testing
To ensure it remains secure, efficient, and reliable, implementing a set of best practices for security testing is essential. These practices are designed to uphold data integrity, confidentiality, and overall system safety. Here are the key strategies:
-
Restrict Unnecessary Network Services
Block all unnecessary network services and their respective ports on the cloud server. This step minimizes the potential entry points for attackers.
-
Control Access to Speed Layer Components
Ensure only authorized IP addresses can access the components. This approach significantly reduces the risk of unauthorized access.
-
Enforce Secure Session Management
Implement policies that promote secure session management. These should include no session reuse and automatic session termination after a set time interval, enhancing the security of connections.
-
Utilize Expiration Mechanisms for Sensitive Data
When accessing sensitive information, employ an expiration mechanism. This ensures that keys and access privileges are set to expire and are automatically removed if not used within a designated timeframe, adding an extra layer of security.
-
Configure Firewall Rules Strategically
Set up firewall rules to limit incoming traffic, based on specific IP addresses or ranges. This helps in preventing unauthorized access and mitigating potential external threats.
-
Implement End-to-End Encryption
Use robust encryption methods, such as Azure Key Vault and Managed Identity, for end-to-end message security. This practice ensures that sensitive data is protected during transmission and stored within Speed Layer components.
-
Develop and Use Appropriate Frameworks and Utilities
Create and utilize suitable frameworks and utilities to thoroughly evaluate components like Service Bus, Function App, and Redis Cache. This is crucial for identifying and addressing vulnerabilities effectively.
By adhering to these best practices, the security of the Cloud Speed Layer can be significantly enhanced, ensuring the safe and efficient operation of cloud-based systems.

How can QASource Help?
QASource has developed specialized frameworks and utilities to identify and address security vulnerabilities within the Cloud Speed Layer. These tools are designed to analyze the layer's components in-depth, ensuring a comprehensive security assessment. Our dedicated security team at QASource maintains and updates these utilities, aligning them with the most recent vulnerabilities.
Our experts possess a deep understanding of Cloud Speed Layer security testing. We are committed to ensuring that our client's data and infrastructure are thoroughly protected against the threats posed by cyber attackers. This commitment to excellence in security testing guarantees the safeguarding of our clients' digital assets.
Conclusion
The Speed Layer, often an internal component of systems with no direct external interface, must be more valued regarding security testing. Yet, its role in managing substantial volumes of real-time data makes it a prime target for cyber attacks. It's crucial to recognize the importance of securing the Speed Layer; failing can lead to severe consequences like potential harm to an organization's reputation and various legal ramifications. Ensuring robust security is a precaution and a necessity in safeguarding valuable digital assets.
Have Suggestions?
We would love to hear your feedback, questions, comments, and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com




