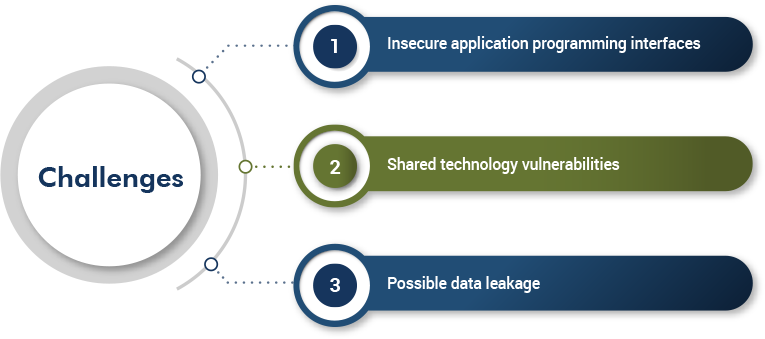
SECaaS Challenges
Adopting SECaaS needs expert monitoring as it has similar challenges as that of using cloud services. The following are a few challenges that an end user may face:
Key Takeaways
- SECaaS enables you to perform risk management by making effective action plans for security
- You can continuously monitor the networks and application from anywhere
- QASource can act as your valuable security solutions partner and coordinate with the SECaaS provider to ensure product security
How QASource Can Help
SECaaS is definitely a boost to organizations. The following are essential activities that QASource can assist you with:
- Access control of the data, system, and server environment
- Continuous network and application monitoring
- Risk assessment and updates
- Incident response participation and reporting
- Managing network services with SECaaS and CSP
- Contingency planning policy, procedures, and plans
- Information flow enforcement
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com