Due to the rapid shift towards digital platforms, organizations are facing a growing number of security threats that can compromise their sensitive data and intellectual property. As the number of applications and digital assets within an organization increases, so does the complexity of managing user access. According to Verizon's data breach investigation report, 81% of data breaches occur due to stolen or weak passwords. This issue can be prevented with the help of Access Management. Access management is the practice of ensuring that the right individuals have the appropriate level of access to digital assets within an organization.
What is Access Management?
The process of detecting, monitoring, regulating, and managing allowed or defined individuals' access to a platform, application, or any other IT component is known as access management. It is used to authenticate, authorize and audit access to applications and IT systems. It creates a security layer between individuals, software services, and data.
Uses of Access Management
Here are some of the uses of Access management:
- It helps to authenticate, authorize, and review access to applications.
- It ensures that the right user has access to the right resources.
- It also helps to control the critical information within the organization.
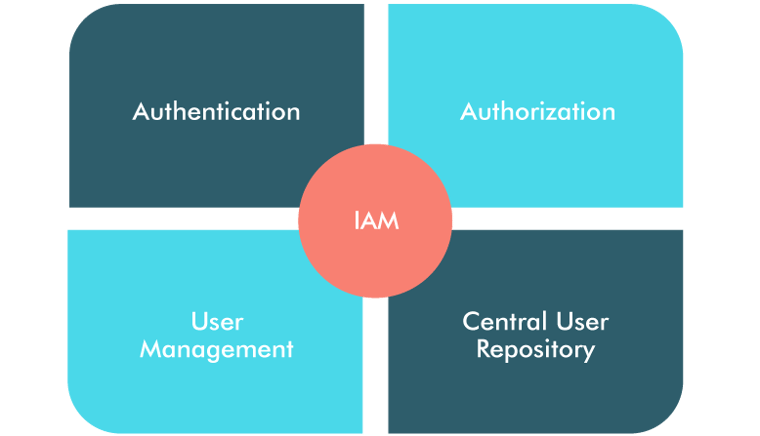
Types Of User Authentication

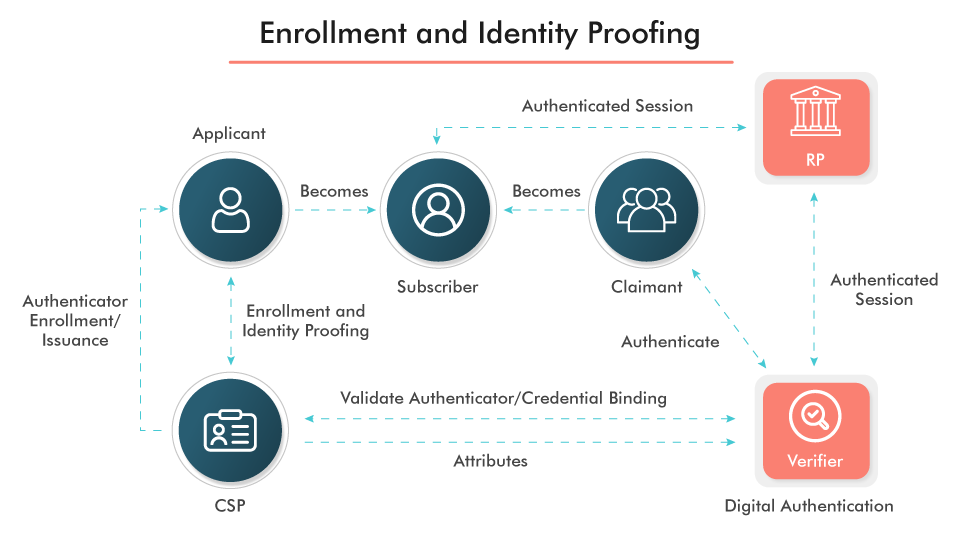
Every individual needs to prove their identity to the server to get authenticated. Users can authenticate their identity by:
- Password, Pin, Security answer, MFA (multi factor authentication), etc.
- Access card, Smart card or Physical key
- Static Biometrics (Fingerprints, Retina, or Face Recognition)
- Voice pattern
Types of Authentication Vulnerabilities
Errors in code or logic can create vulnerabilities in the authentication process and vulnerabilities in the authentication process cause many security issues, resulting in malicious activities in the application.
The most commonly faced authentication issues are:
-
Weak Password
Hackers can try multiple combinations of passwords (dictionary attacks) until they get the correct password. The application should not allow users to create passwords that can be guessed easily.
-
Weak HTTP Authentication
When simple web authentication is implemented in the application, the user name and password are sent along with the HTTP request. Hackers can easily retrieve the username and password from URL strings.
-
SQL Injections
SQL injection can steal information from the database if it is not protected properly. Attackers can send malicious SQL code along with the input to manipulate or steal crucial information.
-
Inappropriate User Session
There are various vulnerabilities related to poor session management such as no session timeout, session cookies without an HTTP flag, and poor session validation.
-
Parameters In URL Not Encrypted
When a user session is created, we include sensitive information in application URL strings such as customer id, quote id, etc. We need to ensure that all these values in the URL are in encrypted form as hackers can use this information and replace it with random values.
Authorization Overview
Authorization is a process by which a server determines if the client has permission to use a resource or access a file. Organizations determine the resources where authorization is required. Most marketing pages on the internet have no authorization. Authorization is applied with the combination of authentication. The user is authenticated for his identity first and then authorization is given.
Types of User Access
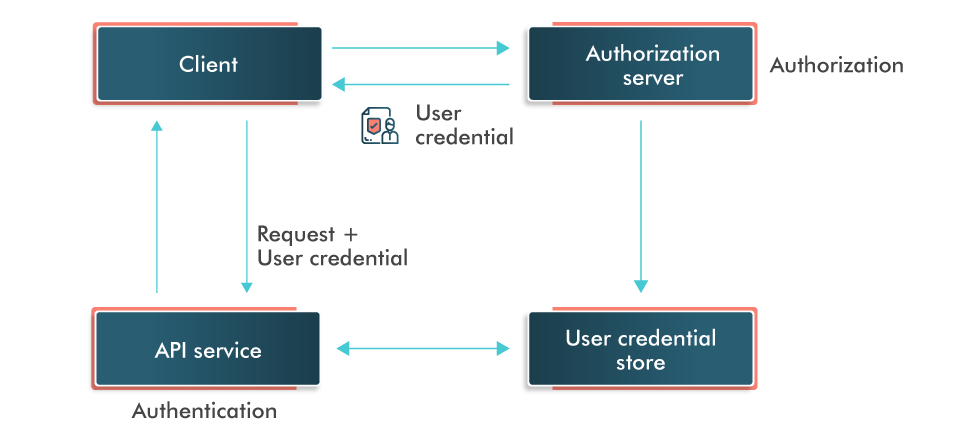
Role-based Authorization: Authorization can be provided based on the user's role and what a user needs in the application.
Access Control List: ACL is a list of rules that determines particular access to resources for the end users. This is used to filter specific users and allow or deny resource access as per the rule.
Token Authorization: Secure token authorization can be provided to the user to access resources in the application. The token key along with the request is sent to the server and resource access is granted to the user after successful verification.
OpenID Authorization: In this authorization, no password or token is required to access a particular resource.
Tools for Access Management Testing

-
ZAP
-
An open-source tool that is used for scanning web applications. It supports both active and passive scans.
Benefits: It has inbuilt checkpoints for broken access and weak authentication in the tools. With the help of these checkpoints, it can verify all the security vulnerabilities related to access control testing.
-
-
Burp Suite
-
This tool is used to perform security testing of web applications. It supports the entire security testing process, from initial mapping and analysis of an application's attack surface to finding and exploiting security vulnerabilities.
Benefits: With the help of this tool, we can verify thousands of payloads to verify a broken access control attack.
-
Access Management Best Practices
Let us now look at some of the best practices related to access management:
- Ensure only legitimate users can log into the application.
- Create a process for detecting and responding to vulnerable components.
- Perform access control checks on every request or functionality being accessed.
- Centralize the logic for handling failed access control checks.
- Verify application after bypassing authentication schema.
- Check the session management and session hijacking.
Access Control Attacks
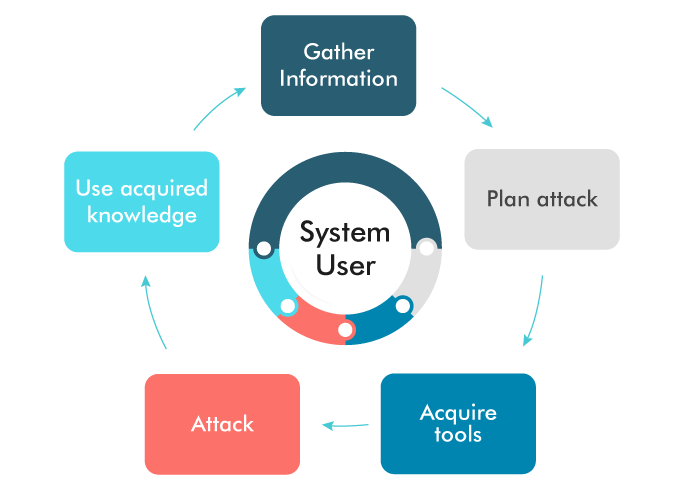
Here is how attackers plan to take control of user access:
- Attackers use various social engineering techniques to convince users to provide sensitive information.
- Social engineering is used to manipulate and influence a user in order to gain control over the computer system. A hacker might use the phone, or email to gain access.
- They focus on human error to gain access to the software system.
Types of Access Control Attacks
Here are the various types of access control attacks that hackers use:
- Spoofing or Phishing email: Phishing emails are sent to a large number of users to click on a malicious link or to provide sensitive information.
- Pretexting: Here attackers can pretend to be someone else and ask a series of questions from the users to gain sensitive information.
- Password Attacks: There are various methods where attackers use random dictionary passwords to gain access of the system. This will bypass admin security and the entire system can be compromised.
Conclusion
Access control attacks can harm an individual in the form of identity theft or other fraudulent use of the information, however, we can prevent such security breaches if we implement broken access control testing. QASource helps reduce such security breaches and embraces security for authentication and authorization vulnerabilities so that issues can be addressed preemptively. To know more about identity and access management security testing, contact QASource now.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com