MFA creates multiple layers of protection that make it harder for any unauthorized user to access an application. If one layer breaks, the attacker still has to break through more barriers to get access, which is not an easy task.
Multi-factor authentication (MFA) is a security technology that allows a user to log in or perform other transactions only when they complete multiple authentication steps.
MFA creates multiple layers of protection that make it harder for any unauthorized user to access an application. If one layer breaks, the attacker still has to break through one or more barriers to get access, which is not an easy task.
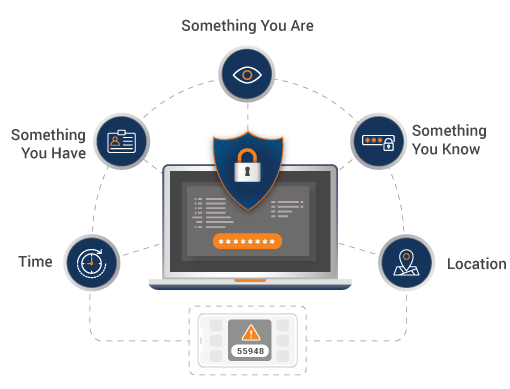
MFA Factors
-
Knowledge: Something a user knows, for example, password, PIN, or a pattern
-
Possession: Something a user has, for example, safety tokens
-
Heritage: Something unique to a user, for example, fingerprint, retina, or voice recognition
-
Place: Based on the user's geographic location
-
Time: A time-based window of opportunity to authenticate like one time password
MFA Authentication Methods
SMS Token Authentication
A PIN is sent to the user's registered phone number and then used as a one time password (OTP).
Email Token Authentication
This is similar to SMS tokens, but the PIN/code is sent via email.
Hardware Token Authentication
A hardware token is inserted into the device.
Software Token Authentication
An authentication application is installed on a mobile device, and the token generated is inserted in the application (just like a hardware token).
Phone Authentication
Randomly generated one-time password (OTP) via automated phone calls.
Biometric Verification
People with devices having biometric authentication, such as fingerprint ID or facial recognition, can use this to confirm their identity.
Testing MFA-Implemented Applications
When testing applications using multi factor authentication, the following approach is helpful:
- Understand Authentication Solutions: Understand what all MFA solutions are integrated with the application.
- Security Requirements: Work with your security and IT teams to understand how MFA aligns with your company’s security requirements.
- Compliance Requirements: What audit requirements are being affected by an MFA implementation.
- Device Requirements: Check if your company’s mobile device policies place any constraints on your MFA implementation.
- User Considerations: Understand how implemented MFA can impact the various user roles.
Benefits of Using MFA
-

1. Better Security
Multiple layers of defense provide additional protection to consumers and employees
-

2. Achieve Compliance
Specific to organization to mitigate audit findings and avoid potential allegations
-

3.No Data Compromised by Lost Devices
Device-based multi-factor authentication ensures that lost devices do not lead to compromised access or data
MFA Trends
Industries Using MFA
- Finance: The finance industry has been using MFA for a long time. For example, whenever you use an ATM, you are using 2FA as you need your PIN (something you know) and your ATM card (something you have) to access your bank account.
- Healthcare: MFA ensures that healthcare organizations have high standards of password security and are compliant with industry regulations.
- Government Agencies: Government employees are prime targets for cyberattacks because they have access to sensitive data such as financial, economic, and military records.
- eCommerce: There are enormous chances of an eCommerce website being attacked on a large scale as it is one of the biggest markets and has a lot to lose.
Popular MFA Hardware and Software

-
Software
- Duo Security
- Google Authenticator
- LastPass
- Microsoft Authenticator
-
Hardware
- Yubikey
- RSA SecurID
QASource can be your go-to partner in setting up and efficiently testing your application with MFA hardware and software. Our engineers have a great understanding of the above-mentioned approaches to provide effective testing solutions. Want to get started? Contact QASource today.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com


