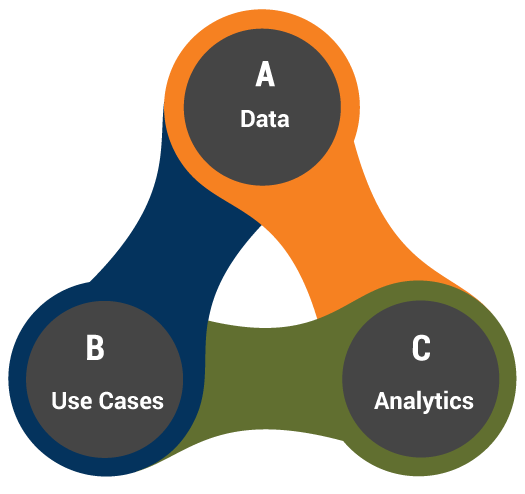
Main Components of UEBA

-
User Monitoring and Data Collection System
The user and entity activities are monitored for anomalies. Different behavioral factors are analyzed from generally visited websites to typically used applications.
-

Machine Learning System
A large amount of data generated by user monitoring systems is used and analyzed by machine learning system to detect anomalies.
Use Cases
UEBA vs SIEM
Security Information and Event Management (SIEM) tools are also an option for teams looking to understand user behaviors.
The following are the key differences between UEBA and SIEM tools.
| UEBA | SIEM |
|---|---|
|
Operates in real-time.
|
Point-in-time analysis of event data.
|
|
Machine learning models and algorithms are used to analyze data in real time.
|
Manual effort is mostly required to analyze the data.
|
|
Provides risk scoring that rank the threats efficiently.
|
Alerts are generated based on events that may or may not be malicious.
|
|
Processes huge amounts of structured and unstructured data.
|
Processes structured logs only.
|
Sample UEBA Report
Security Events
Risk Levels
- Medium
- High
Anomalous Reasons
- Suspicous Endpoint
- Unusual User Location
- Unusual User Login Time
- Unusual Application Access
Anomalous Activity
| Risk Level | Timestamp | Result | User | Application | Access Device | Second Factor |
|---|---|---|---|---|---|---|
|
High
Unusual Application Access The activity is: Normal Unnormal |
10:39 PM
January 04, 2021 |
DeniedEndpoint is not Trusted
|
Jmarty
|
Python Web SDK (kmb)
|
> iOS 14.4
|
Passcode
|
|
High
Unusual Application Access |
08:24 PM
January 04, 2021 |
DeniedEndpoint is not Trusted
|
Psmith
|
Microsoft OWA 166
|
> iOS 14.3
|
Passcode
|
|
Medium
Suspicious Endpoint |
06:05 PM
January 04, 2021 |
DeniedEndpoint is not Trusted
|
Bjoseph
|
Juniper SSL VPN 10
|
> iOS 13.5
|
Passcode
|
Best Practices
- Identify the sources of data for user behavior, network flows, and system logs.
- Enable active directory auditing to track user activity on your systems.
- Audit the systems with sensitive information.
- Track details on account creation and account logins.
- Frequently review account permissions.
- Provide UBA solution with all the data.
- Regularly review UBA reports and investigate incidents.
- Create relevant use cases and use datasets to find security solutions.
- Utilize tools like Microsoft Advanced Threat Analytics and Incydr.
Have Suggestions?
We would love to hear your feedback, questions, comments and suggestions. This will help us to make us better and more useful next time.
Share your thoughts and ideas at knowledgecenter@qasource.com